At mayamaya.ai, security and data privacy are not just features; they are foundational to our AI talent management platform. Explore our certifications and practices.
Independently verified assurance of our security posture.
How we protect your data every day with robust controls.
How we protect your data every day with robust controls.
MayaMaya (Catenate Corp), headquartered in Frisco, Texas, is a pioneering AI-Talent management company offering subscription-based SaaS solutions to its clients globally. MayaMaya has been instrumental in driving successful talent management of its clients by enabling them to identify key areas to focus for decision-makers within their organization.
MayaMaya prioritizes security, dedicating itself to the safeguarding of information against both intentional and unintentional misuse. This commitment extends to protecting the information of customers, partners, vendors, and other third parties. Proudly, we have implemented a comprehensive Information Security Management System (ISMS) that aligns with the rigorous standards of SOC2 Type II. We conduct periodic 3rd party Penetration testing to identify vulnerabilities & harden our landscape. These certifications and practices underscore the effectiveness of our control framework, highlighting our commitment to security, availability, and confidentiality controls surrounding our services.
Our security strategy is bolstered by a combination of expert security personnel, top-tier tools, and third-party services encompassing assessments, control reviews, technical evaluations, and testing. Continuous control monitoring across our environment is enhanced by additional security measures to counteract exploitation attempts. We rigorously evaluate our service providers’ security practices, requiring them to hold relevant certifications and conduct control analyses to effectively manage third-party risks.
Security Fundamentals
Our comprehensive risk management and compliance framework underpins our information security program. Central to this program is our ISMS, which facilitates the assessment, management, monitoring, and mitigation of our information security risks through:
• Leadership
• Planning
• Support
• Security Operations
• Performance Evaluation
• Continuous Improvement
Our Information Security comprises of policies and procedures for managing sensitive information, addressing access, handling processes, and the technology used. This approach helps cultivate a security-aware corporate culture at MayaMaya.
Our information security team is a diverse collective of experienced professionals specializing in data governance, compliance, risk management, cyber threat- intelligence, breach preparedness, security operations, and offensive security. Team members hold prestigious certifications, and we maintain strong ties with academic and governmental sectors, ensuring continuous adoption of best practices through ongoing education and training.
Our security processes and controls are integrated into our entire lifecycle, making security an inherent part of our operations. We adhere to the relevant Risk Management Standards, conducting continuous risk assessments in collaboration with risk owners across MayaMaya’s business units.
All employees and contractors undergo training to ensure compatibility with our corporate culture. Continuous, dynamic security awareness training is mandated to nurture a security-focused mindset, embedding security professional practices.
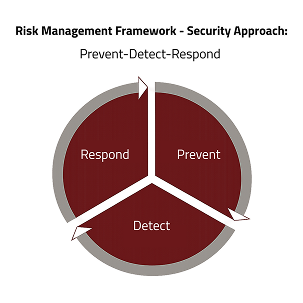
Our Preventive security measures form a critical component of our layered security strategy, encompassing:
• Critical Assets: Identifying valuable business intelligence, customer data, and access credentials, ensuring access is appropriately provisioned.
• Data Protection: Implementing Multi-Factor Authentication (MFA) and/or Single Sign-On (SSO), encrypting customer data at rest with AES256, and securing browser-client communications minimally with TLS 1.2.
• Application Protection: Hosting in Azure with comprehensive security controls and employing automated operations to minimize human interaction with critical systems.
• Cloud Security: Utilizing multi-layered security provided by cloud architecture and firewall functionalities, augmented by third-party Web Application Firewalls and DDOS protection services.
• Network Security: Protecting our corporate and cloud environments with advanced gateway devices and employing robust access control mechanisms and processes to limit unauthorized access to network resources.
• End Point Devices: Ensuring devices operate with state-of-the-art malware protection, incident detection, and response capabilities, alongside regular patching and updates.
• Perimeter Defense: Employing a robust network infrastructure with limited access to minimize vulnerabilities.
• Physical Protection: Implementing stringent physical security measures at corporate offices and relying on cloud service providers for physical security of cloud infrastructure.
Our detection strategies employ leading-edge endpoint protection systems and sophisticated threat detection techniques, including:
• Threat Detection and Analysis: Utilizing comprehensive endpoint protection that reports to a central monitoring portal, allowing for the immediate disconnection of compromised systems.
• Network and Infrastructure Security: Defending against DDOS, employing Web Application Firewalls (WAFs), and implementing firewalls and intrusion detection systems to monitor and manage threats efficiently.
• Logging and Monitoring: Maintaining logs for performance, operations, and security events, with dedicated teams responsible for monitoring and promptly addressing anomalies or security incidents.
• Fraud and Abuse Detection: Operating a dedicated fraud and abuse team to monitor application activity, employing custom-built tools to detect and respond to anomalous actions in real-time.
1. MayaMaya has developed a comprehensive response framework to effectively address and manage security events, ensuring swift and efficient resolution.
2.Our incident response and crisis management procedures are well-defined, enabling swift and effective action in various scenarios. We prioritize assessment, containment, eradication, and recovery, supported by ongoing training and simulation exercises.
3.Our Response strategies include: Incident Response Plans: Maintaining clear plans that outline the steps to take in the event of a cybersecurity incident. Communication Protocols: Establishing communication channels to inform stakeholders and regulatory bodies as necessary. Recovery Procedures: Implementing strategies to restore normal operations and minimize the impact of the incident.
MayaMaya is undergoing a comprehensive SOC 2 Type II attestation.
MayaMaya proactively addresses security risks, conducting regular vulnerability assessments, and maintaining a risk register for comprehensive risk tracking. Our approach ensures timely remediation based on the impact of identified risks.
For security-related inquiries or concerns, please reach out to us at security@mayamaya.com. Our team is dedicated to addressing your questions and ensuring the security of your information.
The purpose of this policy is to provide guidance that limits the use of encryption to those algorithms that have received substantial public review and have been proven to work effectively. Additionally, this policy provides direction to ensure that Federal regulations are followed, and legal authority is granted for the dissemination and use of encryption technologies outside of the United States.
Ciphers in use must meet or exceed the set defined as “AES-compatible” or “partially AES-compatible” according to the IETF/IRTF Cipher Catalog.
The use of the Advanced Encryption Standard (AES) is strongly recommended for symmetric encryption.
The use of the RSA and Elliptic Curve Cryptography (ECC) algorithms is strongly recommended for asymmetric encryption.
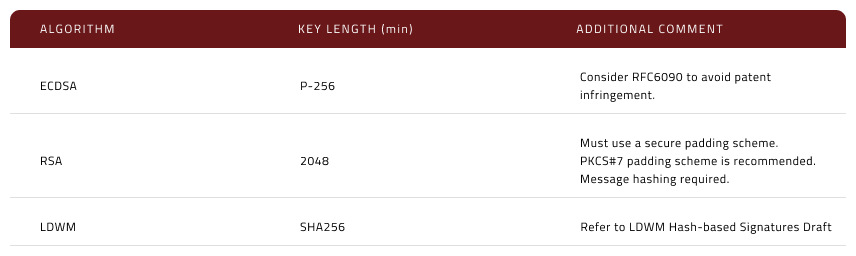
Mayamaya adheres to the NIST Policy on Hash Functions.
• Key exchanges must use one of the following cryptographic protocols: Diffie-Hellman, IKE, or Elliptic Curve Diffie-Hellman (ECDH).
• End points must be authenticated prior to the exchange or derivation of session keys.
• Public keys used to establish trust must be authenticated prior to use. Examples of authentication include transmission via cryptographically signed message or manual verification of the public key hash.
• All servers used for authentication must have installed a valid certificate signed by a known trusted provider.
• All servers and applications using SSL or TLS must have the certificates signed by a known, trusted provider.
• Cryptographic keys must be generated and stored in a secure manner that prevents loss, theft, or compromise.
• Key generation must be seeded from an industry standard random number generator (RNG).
All end user laptops and desktop drives shall be encrypted through a centralized encryption tool.
Compliance Measurement Mayamaya’s Infosec team will verify compliance to this policy through various methods, including but not limited to business tool reports, internal and external audits, and feedback to the policy owner.
Any exception to the policy must be approved by the Infosec team in advance.
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment.
Mayamaya has a structured and well tested mechanism to react appropriately to any actual or suspected incidents relating to information systems and information.
Mayamaya continuously monitors multiple telemetry that are indicators of compromise that breach security and/or confidentiality of information. we continuously identify,
report, investigate and remediate any incident.
MayaMaya implements a risk-based security approach that focuses on identifying and prioritizing the most critical cybersecurity risks. It is based on continuous monitoring, data-driven assessment, and adaptive control implementation.
By adopting a risk-based approach, we make informed decisions about where to allocate our cybersecurity resources and prioritize efforts based on the most critical assets and vulnerabilities.
We follow industry standard Policies & procedures for managing, reviewing and validating user access to information systems. We have a layered security approach to secure customer data, loss of customers or business partner confidence, reputation damage, and to meet Regulatory compliance.
• It is the policy of MayaMaya that access to PII and all other sensitive data will be allowed only for persons authorized by security and privacy Policies/ Rules.
• Any person who does not meet one of these conditions shall be prohibited from access.
• Each user shall strictly be granted role-based access using a unique ID or account.
• Sharing of accounts without explicit permission of the Security team is a security violation.
• User rights are to be granted using the principle of least privilege and need to access basis.
• Information and records relating to clients will be stored securely in the US and will only be accessible to authorized staff and contractors.
• Information will be stored for only as long as it is needed or required by statute and will be disposed of appropriately. It is MayaMaya’s responsibility to ensure all personal and company data is non-recoverable from any computer system previously used within the organization, which has been passed on/sold to a third party.
MayaMaya provides mechanisms to collaborate between internal users and external partners. Access will be granted by the Security Team based on:
• Least Privilege: Users will only be granted least privilege access, for the purpose of executing their responsibilities and duties.
The right to access such information shall not be granted unless there is a legitimate business need
• Segregation of Duties: Users shall not be able to grant themselves rights. Administrative accounts shall be monitored. To the maximum extent logs shall be maintained.
• Role Based Access: Users will be assigned access rights to PII and other confidential information based on functional roles they assume in the course of doing MayaMaya business. Users assigned access to confidential information will be trained specifically on data protection and non-sharing of confidential information (exemption being in the case of regulatory/legal requirements).
MayaMaya has well established guidelines and procedures for masking of data to protect privacy & the secure deletion of information complying with legal requirements and manage data lifecycle effectively within Mayamaya.
• Data Deletion: The permanent removal of data from storage systems, including databases, files, backups, and archives.
• Data Masking: The process of obfuscating or pseudonymizing sensitive data to prevent identification
of individuals while maintaining usability for authorized purposes.
• Sensitive Information: Includes personally identifiable information (PII), financial data, intellectual property, and any other data deemed sensitive by mayamaya.
• Data Classification: Data will be classified based on sensitivity levels (e.g., public, internal, confidential) to determine appropriate deletion and masking procedures.
• Retention Periods: Data retention periods will be defined for each classification level, taking into account legal, regulatory, and business requirements.
• Initiation: Data deletion requests must be authorized by [designated authority or role].
• Methods: Data deletion will be conducted using secure methods to ensure irreversibility and compliance with data protection regulations.
• Documentation: Records of data deletion activities, including dates, methods, and responsible parties, will be maintained for audit and compliance purposes.
• Purpose: Data masking will be used to anonymize or pseudonymize sensitive information where feasible and necessary for operational purposes.
• Techniques: Approved data masking techniques and tools (e.g., encryption, tokenization) will be used to render sensitive data unreadable or unusable for unauthorized users.
• Access Controls: Access to masked data will be restricted to authorized personnel based on the principle of least privilege.